Keyboard clicking in a dimly lit, off-the-grid location, a dark silhouette sits behind multiple monitors with cascading lines of code, conjuring images straight out of a Hollywood thriller. These are the scenes that often come to mind when hearing the word “hacker.”
Yet, many are unaware that there exists a world of hacking that contributes to the security improvement of the items we use every day. While the term “hacking” is typically associated with criminal activities, ethical hackers, known as “White Hat Hackers,” play a crucial role by identifying and reporting bugs and potential exploits to developers and manufacturers, reducing the risk of malicious attacks.
Hacking Tokyo

From January 24 to 26, the world’s largest hacking competition ever, “Pwn2Own Automotive,” was held at Tokyo Big Sight at the Automotive World Tokyo 2024 convention.
On a grand stage bathed in neon lights, accompanied by dramatic music, and with a glistening Tesla Model Y on display, teams of hackers and individual researchers from different nations faced challenge after challenge, infiltrating automotive devices in front of a sprawling audience as the 30-minute timer counted down. Over three days, a total of 49 unknown zero-day security vulnerabilities were revealed.
As the name suggests, the Pwn2Own Automotive hacking competition, held for the first time this year, was exclusively dedicated to automotive components, targeting In-Vehicle Infotainment (IVI) systems, Electric Vehicle (EV) chargers, and more. Japan, recognized for its leading role in automotive technology, was the chosen setting for this groundbreaking event.
Smart but risky
In an era where cars are evolving into smarter machines like many other daily appliances, their increasing interconnectedness through technologies like Bluetooth and Wi-Fi raises pertinent security concerns. Like any smart device connected to a wider network or digital ecosystem, automotive components can serve as access points for nefarious activities, ranging from stealing personal data to potentially gaining control over critical moving parts of the vehicle.
Pwn2Own, which started humbly in 2007 as a competition where hackers aimed to “Pwn” (to control or compromise another device in hacker slang) devices in order to “Own” and claim it as a prize, has evolved significantly. Organized by Zero Day Initiative of Trend Micro, the Pwn2Own hacking competition is now held multiple times a year throughout various locations around the world, attracting researchers from multiple countries and offering substantial cash rewards for successful breaches. The Tokyo competition’s combined payout exceeded a staggering $1.3 million USD, marking a historic high for the competition.

A vital aspect of the Pwn2Own process is the immediate disclosure of exploited bugs to the original vendors after each successful round to facilitate timely patching before the details go public. This collaborative exchange stands at the forefront of cybersecurity research, positioning Zero Day Initiative as one of the world’s largest bug bounty programs.
Plugging into the world of hacking
The question arises: do White Hat Hackers ever cross over to the dark side and become criminal hackers? On the Pwn2Own stage, Dustin Childs, the main spokesperson of the competition, explained that although that does happen, you’ll find that the opposite is in fact more common, where criminal hackers transition into the world of ethical hacking. Dustin also states that, with enough time and money, anything can be hacked. Although making a product unhackable is impossible, developers try to make hacking the product so resource-consuming that malicious agents turn to other, easier targets. What makes a good hacker? The most common trait you’ll find is having a curious mind and a desire to gain some kind of advantage (such as when hacking a video game for a better chance to win).
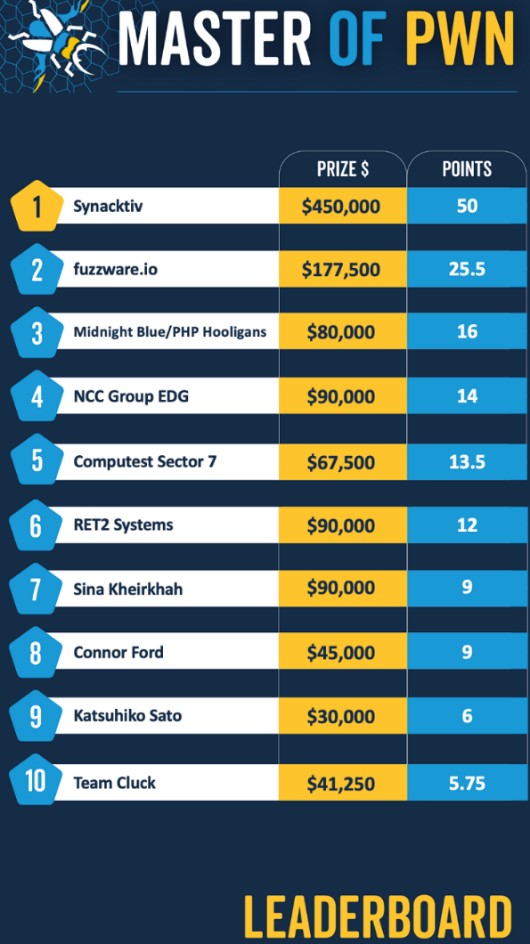
A standout moment over the three-day competition was Synacktiv executing a 3-bug chain against the Tesla Modem on day 1 and successfully attacking a Tesla Infotainment System using a 2-bug chain on day 2. Crowd-pleasing demonstrations included NCC Group EDG showcasing a playable version of the classic video game DOOM on an In-Vehicle Infotainment system using a 2-bug chain. (You can check out the full results on the Zero Day Initiative blog: https://www.zerodayinitiative.com/blog)

From ZDI blog :https://www.zerodayinitiative.com/blog/2024/1/24/pwn2own-automotive-2024-day-two-results
“Master of Pwn”
On the third and final day of the competition, the coveted title of “Master of Pwn” was claimed by the French hacking team Synacktiv, who walked away with an impressive $450,000 USD in combined rewards and a one-of-a kind robot-shaped trophy.
The next Pwn2Own is scheduled for March 20–22 at the CanSecWest Applied Digital Security Conference in Vancouver, the birthplace of the original Pwn2Own. Additionally, Zero Day Initiative plans to keep the engines running and bring Pwn2Own Automotive back to Japan in 2025, so stay tuned for more hacking excitement next year.
VicOne Corporation
https://vicone.com/













